But actually hacking wifi practically is much easier with a good wordlist. But this world list is of no use until we don’t have any idea of how to actually use that word list in order to crack a hash. And before cracking the hash we actually need to generate it. So, below are those steps along with some good wordlists to crack a WPA/WPA2 wifi. Jun 07, 2013 In this tutorial I’ll show How to hack a WPA/WPA2 Wi-Fi connection through a bootable USB. Download beini.iso 3. UNetbootin software to make your USB drive bootable. Download UnetBootin for Windows, Mac or Linux 4. A Dictinary File For WPA 2 Crack. How to Hack WiFi Password (WEP/WPA/WPA2/+PSK) UPDATED WORKING 100. WPA2: Wi-Fi Protected Access II (WPA2) significant improvement was the Mandatory use of AES(Advanced Encryption Standard) algorithms and CCMP(Counter Cipher Mode with Block Chaining Message Authentication Code Protocol) as a replacement for TKIP. Also Read Crack WPA/WPA2 WiFi Passwords With Wifiphisher by Jamming the WiFi. How Fluxion works? Jan 6, 2016 - Download Xiaopan OS for free. Easy to use pentesting distribution for wireless security enthusiasts. Xiaopan OS is an easy to use software package for beginners and experts that includes a number of advanced hacking tools to penetrate WPA / WPA2 / WPS / WEP wireless networks. Based on the Tiny. I have downloaded the Rainbow Tables. Beini gives you the same tools that hackers use to test your wireless network and patch security holes, making your home network more secure from the inside out. The first thing you’ll notice is that this is a very light and fast Linux distribution – you’ll be able to run it off a small 100MB USB key (we suggest having more space free.
If you are unable to Hack WPA / WPA2 WiFi network using WPS Feature, then you have to crack actual WPA / WPA2 encryption. In this hacking process, handshake packets are the only packets which helps in cracking the network. They contain data that can be used to check that WiFi password / key is valid or not. Handshake packets are the 4 packets, which are communicated between the client and the router, when the client connects to the network. These handshake packets can be used to crack WPA / WPA2 key.
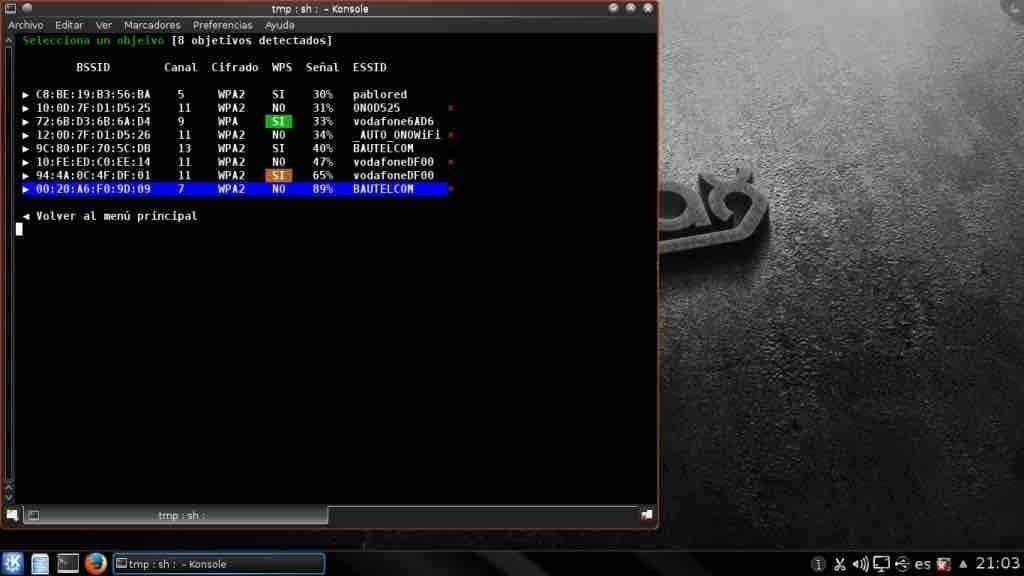
Steps to Hack WPA / WPA2 WiFi Network using Word List Attack
Enable Monitor Mode of Wireless Interface Card.
Capture handshake packets using airodump-ng in Kali Linuxagainst your target network and store the data in a file called hack_wpa_handshake.
Now wait for the handshake packets to be captured. Handshake packets will only be sent when a new client is connected to the network. So, wait until new client is connected to the network.
OR
Alternatively you can use De-authentication Attack, where existing client is disconnected from the network and that client will automatically try to connect to the network again. Once that client is re-connected, handshake packets will be send in the air and then we can capture those handshake packets.
Once the new client is connected to the network or the existing client is disconnected and reconnected to the network, we will receive WPA handshake which is stored in a file called hack_wpa_handshake
Create a word list that contains the large number of passwords / keys
.
Once we have a handshake packet, we will create a word list document that contains password. This document is created usingcrunchtool.Go through the passwords in word list document one by one and use them with the handshake to check that whether password in the document is valid or not.
Use handshake packets to crack WPA/WPA2 password
For cracking WPA/WPA2 password, we will use tool named aircrack-ng. Aircrack-ng will unpack the handshake packet and will match the wordlist passwords one by one with the handshake packet.
There are multiple ways to crack WPA/WPA2 passwords using wordlist attack. Some save the cracking progress and some does not save the cracking progress.
Use aircrack-ng to run wordlist attack to crack WPA/WPA2 passwords without saving cracking progress
In the above command:
- aircrack-ngis the name of the program
- hack_wpa_handshake-01.capis the handshake file which we captured before
- -w PasswordList.txtis the name of my word list document, which contains large number of passwords
aircrack-ng tool runs through the word list document, match each word in the word list with the handshake packet one by one. And at the end, we are able to find the key “abc12345” which is our WiFi network key
For big word list documents, it may takes many hours / days to try all the possible passwords. There could be much bigger dictionaries, that can take many many days to crack the passwords. If we quit aircrack-ng during the process and run the command again, it will lose the session and will start the cracking session from scratch.Save cracking progress while cracking WPA/WPA2 passwords using John the Ripper
In this attack, we will save the cracking session while running aircrack-ng command. So, if we quit aircrack-ng and come back after some time then our session will still be there and we can start the session from where we left. We can save our cracking session usingpassword cracking tool named john the ripper
Here
- johnis the name of the password cracking tool
- –wordlist=PasswordList.txtis the name of the wordlist, which is stored in our current working directory
- –stdoutdisplay this wordlist on the terminal screen
- –session=hackrouter will store the session of john the ripper. Session name is hackrouter
- |using this pipe character (vertical bar), we will redirect the wordlist output and use it as an input to aircrack-ng
- -w – , in this -w attribute, we normally gives the wordlist document name but this time we will use the output generated by john command. And this can be done by using just the – (dash) instead of the wordlist document name
- -b 62:23:6A:96:69:73is the MAC address of my target network
- hack_wpa_handshake-01.capis the name of the handshake file
When john the rippercommand run, it will read all the passwords from a file PasswordList.txt, it will pipe them into aircrack-ng . Aircrack-ng will read these passwords and start cracking. Then when we exit at the middle, john the ripper will store this session in a file named hackrouter.
Now next step is to resume the session using this command
In the above command, we are telling john the ripper to restore the session from where it left last time. And this is stored in a session named hackrouter. This method allows you to stop the attack and start the attack whenever you want.
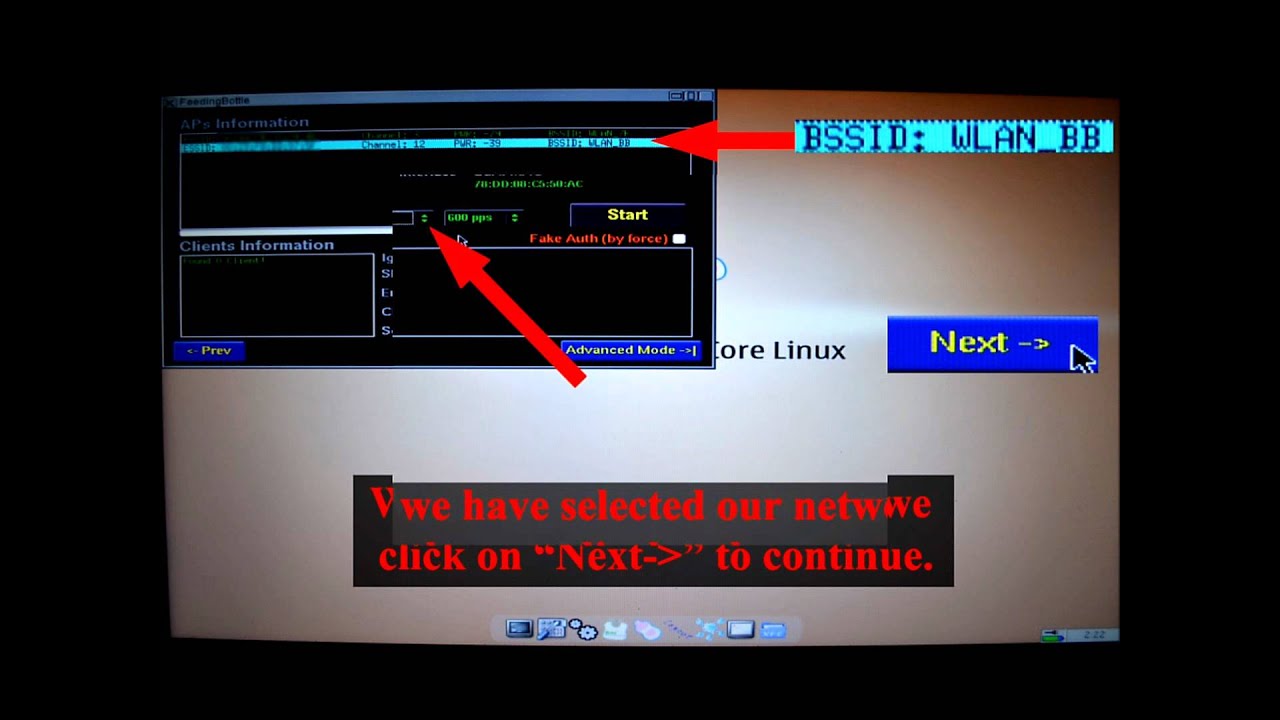
Beini is a small Linux distribution that packs a punch. it is based on Tiny Core Linux. It offers an array of WiFi security audit tools. Beini is easy for newbie to used compare to BackTrack, which is the popular system used to crack WEP/WPA. Beini include packages: Minidwep, Aircrack, Inflator, Reaver, Feeding Bottle, Wifite
*This guide is for your own educational purpose. Hacking or Cracking other people wireless network is illegal and against law. We advice you do not attempt to attack wireless network other than your own.
Download the latest Beini system.
Download UNetbootin
. (Note: Do NOT use the latest version, here we use 377) UNetbootin 377

Format your USB as FAT32.
Create a new folder on your desktop, extract the ISO file that you downloaded in step 1 into that folder.
Open UNetbootin and setup the following
Crack Wpa2 Beini Free Download
(~ means the full Path of a Folder): Kernel: ~bootbzImage Initrd: ~boottinycore.gz Options: ~bootisolinuxisolinux.cfg (you can change these options manually, for example: change the language (e.g. en.utf8). Note: If the USB does not load you should add the following kernel boot parameter waitusb=8 to potentially fix the problem. Note: Make sure you select the correct USB drive.
Crack Wpa2 Wifi
After you see “Installation Complete, Reboot (Current)”, you can reboot the computer and select boot from your USB from BIOS.